#Code Division Multiple Access
Explore tagged Tumblr posts
Text
CDMA Full Form (Code Division Multiple Access)
What is CDMA (Code Division Multiple Access)? Many radio communication systems employ the channel access technique known as code-division multiple access (or CDMA). numerous access technologies, such as CDMA, allow numerous transmitters to deliver data simultaneously over a single communication channel. This makes it possible for several users to share a frequency band (see bandwidth). CDMA Full Form…
CDMA Full Form: Code Division Multiple Access
CDMA is a wireless communication technology where multiple users share the same frequency band using unique codes, ensuring secure and efficient data transmission.
#CDMA Full Form#Code Division Multiple Access#History of CDMA#Uses of CDMA#What is CDMA#what is cdma#what is gsm#what is 2g#what is 3g#what is 2g?#what is 3g?#what is lte#what is gms#what is fdma#what is cdma ?#what is the full form of cdma?#what is code division multiplexing#what is code division multiple access#what is code division multiplexing with example#what is cdma explained with mathematical equations#what kind of#what is the principle behind working of cdma systems#what does gsm mean#what does cdma mean
0 notes
Text
Heavenly Archives- Calamity 06

AN: Sylus is Hua Cheng coded. Fight me. I dare you. Tried something new, let's hope formatting did not kick my ass.
Pairing: Sylus x Reader
"No water is enough when you have crossed the sea, No cloud is beautiful but that which crowns the peak. I pass by flowers that fail to attract poor me, Half for your sake and half for Taoism I seek." - Yuan Zhen
Yearning Event

HEAVENLY ARCHIVES: CLASSIFIED RECORD [CALAMITY PROFILE: 06 / DESIGNATION: SYLUS] ACCESS LEVEL: RESTRICTED (CELESTIAL RANK IV AND ABOVE) COMPILED BY: IMPERIAL RECORDS DIVISION / UNSEALED UNDER ORDER #AX777-B DATE OF PRIMARY INCIDENT: ~1200 cycles prior

Warning
The following document is sealed under Heaven Decree 06-CRIMSON, originally issued 1200 cycles ago following the Sixth Calamity.
This file contains information deemed volatile, heretical, and historically destabilizing by the High Court. Unauthorized access or reproduction of any content within this archive will result in, immediate invocation of the Silent Oath

SUMMARY OF EVENT
The Sixth Calamity, known to common folk as Sylus, launched a full-scale assault on the Heavenly Court approximately 800 years ago, resulting in the complete destruction of the East Pavilion, obliteration of the Warrior God Corps, and the permanent disbandment of the Flame Lotus Order. Casualties remain unnumbered due to ashfall corruption of divine records. The attack was sudden. Brutal. Unprovoked by any known celestial decree.
Only one structure was spared:
a small, unregistered hut located in the lower gardens of the Heaven’s Eastern Watch.
The Calamity halted before it. Witnesses, those who survived, claimed the moment Sylus laid eyes on the structure, the wrath that devoured gods was gone. Just... gone. What power resided in that hut remains unknown.

SURVIVING ACCOUNTS: WARRIOR GODS’ REPORTS
“He saw something. Something sacred. Something from... before.”
“I thought it was the Empress herself. But it wasn’t her body he bowed to.”
“It looked like grief.”
None could agree on the true nature of the site. Some say it belonged to a nymph. Others whispered it was the former quarters of a forgotten imperial concubine. But the most consistent, albeit suppressed, theory, is that it was once the resting place of a young god of justice, long erased from the rolls.

FIELD REPORT: FALLEN WORLD (RESTRICTED TERRITORY)
In an effort to reconstruct a timeline preceding the Calamity, our team was dispatched to the former dominion of Sylus in the Lower Realms.
ORAL ACCOUNT: ORC CAMP, TERRA BONE REGION
“He was mortal back then,” said one orc, self-identified as Talus, former shield-bearer to the house of Sylus. “Lord was young. Just flesh. Walked among the rest of us. Then he saw his love, the justice god. The bright one. And from that moment, nothing else ever mattered again.” [Laughter recorded. Followed by minor static interference.] “Doomed, he was. Ye can’t love a god and survive, aye?”
CULTURAL REFLECTION: FOX TRIBE, EASTERN HOLLOW
“Mortals cannot touch gods,” said the Nine-Tail Elder. “But our lord tried. He gave everything, breath, blood, name, for the one he called his justice.” “When the god was put to trial, stripped of title, cast aside by Heaven, Sylus burned with him. But he was only human. His body broke. His mind fractured. What was left... was rage.”
“That’s what the heavens call a calamity. Grief so powerful it set the sky on fire.”

UNCONFIRMED ANOMALIES:
No divine records remain of a “justice deity” fitting the descriptions collected from the lower realms.
The hut spared by the Calamity has since vanished.
Sylus has not been seen since the day of the assault.
Multiple sealed temples in the Fallen World still bear symbols that match the preserved markings on the hut.

FINAL NOTATION:
Though officially labeled a Calamity, Sylus's actions and motivations remain subject to dispute among celestial historians. Many believe the destruction of heaven was not an act of power, but of mourning.
Of a love made sacrilege. Of a grief no god dared name.
Further investigation is forbidden under Order 497-H. All who speak the name of the forgotten god shall be marked with silence. But still, in the ruined corners of the world, one phrase persists:
“Justice prevails by the hands of calamity, bringing heaven to its knees."
#love and deepspace#sylus x reader#love and deepspace sylus#yearning event#hua cheng is such a legend#I will die on this hill#tgfc au
31 notes
·
View notes
Text
Edward Nigma
Part 1: Arkham Origins/Arkham Shadow
Story:
The future Edward Nigma committed his first crime when he was still in grade school. Constantly belittled and called a moron by his abusive father, he entered a school contest to win everyone's approval; solve a puzzle and win a prize. Nashton broke in late at night and put the puzzle together as many times as possible until he had the winning solution. His father accused him of cheating and beat him for lying.
Undeterred, Edward dedicated himself to learning, and became a skilled engineering and computer hacking genius. He found employment as a member of the GCPD's Cyber Crime Division and became convinced that Gotham's long history of corruption was the result of intellectual and moral failing rather than economics. To "improve" the city's standing, Nashton used his position and skills to coordinate a large network of operatives and compile a large collection of blackmail material connected to prominent Gotham officials.
Before Christmas Eve, Nashton collected and hid extortion data files while also searching for the real identity of Batman, whom he believed was either Harvey Dent or Bruce Wayne. To maintain his cover within the GCPD, Nashton may have cultivated genuine criminal ties himself as he was soon contacted by Black Mask (or so he thought) to distract the vigilante.
Nashton, under the alias of Enigma, used an army of informants to collect a cornucopia of blackmail information about the city's most corrupt individuals. Enigma planned to release this information to the public on Christmas Day, and intended to trigger a chain reaction that would end in Gotham City's collapse.
Enigma recognized Batman as his greatest obstacle and had set up multiple layers of fail safes that included: hiding his servers behind a billboard, planting signal jammers inside the Gotham City Radio Towers that Batman had used to pilot the Batwing, set up dozens of relays across the city, employed an army of Thugs to hamper him at every turn, and had used his informants to hide all of the extortion data that he had collected all throughout Gotham.
Enigma continued to taunt Batman as he attempted to disrupt all of the radio towers, but eventually Batman succeeded. Finally, after destroying all relays, interrogating all informants, and collecting all the data packs, Batman came back to Enigma's HQ and destroyed his server. Enigma accepted temporary defeat, while he claimed that he had held onto the biggest, dirtiest secret that had put his collection of data to shame. Batman later unlocked Enigma's secret room, which revealed several items of interest: newspaper clips that indicated Enigma's research on Batman's identity (With the two main suspects that were Bruce Wayne and Harvey Dent), pressure pads, cages, and one green glowing question mark that would later become the Riddler Trophy. Later, Enigma was deduced to being Edward Nashton, who was the head of the GCPD's Cyber Crime Division, by Alfred Pennyworth in a conversation with Batman in the Batcave.
A coded message within the GCPD Server and Telecom Rooms revealed that Nashton had only recently joined the organization as its Cyber Crime Division head, and revealed that he had only joined the GCPD simply to gain inside information through his newly acquired access to the entire city's infrastructure and files, which was eventually used as extortion data on all of Gotham.
The next day, just as Mayor Hamilton Hill was about to appoint Peter Grogan to replace the deceased Gillian B. Loeb as GCPD Commissioner, various media outlets received envelopes from an anonymous individual containing evidence that implicated Hill and Grogan as having ties with the Maroni Family. It was strongly implied that Enigma had been the one who was responsible, as he had yet to reveal his "biggest, dirtiest secret."
6 days of public protest ensued until New Year's Day, when Mayor Hill resigned from office in disgrace, although he had not ruled out a possible attempt at re-election during the new year. Regardless of whether he ran for office or not, his resignation meant that Grogan did not become Commissioner.
This meant that, ironically enough, Enigma's plans had a profoundly positive effect on Gotham City as they had finally revealed the corruption and conspiracy within Gotham's politics to the world at large, so the public could force their corrupt public officials out of office and appoint more ethical and principled individuals instead. Whether this was Engima's true intention was unknown, though his previous statements of wanting chaos in the streets seem to make it unlikely, as the resolution to the scandal ended on relatively peaceful terms.
Edward Nashton spent the next six months building a personal fortune with his cyber crime skills, while adopting a new persona known as the Riddler; having chosen to theme himself after riddles, after having deemed Batman one when they first made contact and with his interest in riddles becoming reignited after seeing the lengths Batman went to finding his data packs.
Some time during the week of the Independence Day Riots, Riddler snuck into Blackgate Prison and stole Carmine Falcone’s blackmail ledger from his secret vault in Maximum Security, before leaving behind a datapack that contained a message for Carmine. In the message, he gloats that he stole the incriminating evidence and added it to his collection of extortion data, and insinuated an awareness of Carmine’s relationship with his wife, Louisa, and an unnamed illegitimate progeny (possibly Catwoman, as evident by his use of feline-related vocabulary). Anticipating that Batman may find this message as well, he gloated that Batman would always be a step behind him.
Some time after the Day of Wrath, Edward legally changed his last name to Nigma as a call-back to Batman's Enigma alias for him, and would go on to become a notorious criminal in Gotham known for his riddles. In addition to his riddles, Nigma decided to create death traps to kill who he considered to be the less intelligent people of Gotham; while deeming them "entertainment" for true intellectuals who he believed could solve them easily. Riddler even hired henchmen of his own, though he secretly loathes their low intellects; despite this, he had them infiltrate various other criminal cabals to get him information on other villains. Riddler clashed with Batman numerous times over the years, with deaths abundant and his penchant for riddles aggravating the GCPD, and his obsessive need for attention making him leave riddles and clues for Batman to solve and eventually stop him.
Personality:
Edward Nigma was defined by his insanity, inferiority complex, violent behaviour and intense narcissism, likened with hubris. However, he was extremely emotionally immature and his nature was that of an overgrown man-child as he was still traumatised by his cruel childhood and his abusive father who undermined him at every turn. Nigma's image of self-awareness is extremely misguided as he deludes himself into believing that he is a flawless and infallible human "colossus" (or in his own words "The World's Greatest Everything"). Another of his delusions is his incapability to understand his own insanity and when Batman calls him out on this, although he gives a detailed definition he says he suffers from none of the sort. Nigma displays anti-social behaviour and his characteristics, even into adult years are similar to that of an adolescent teenager. Amongst these traits of his childishness are competitiveness, recklessness, stubbornness, pride, rash outbursts, fiery temper, aggressive tantrums and sullenness.
Despite being megalomaniacal, psychopathic and egocentric, at his core Nigma is deeply insecure and emotionally scarred. Having never received the recognition he deserved (or at least believed he deserved), it stands to reason that he pathologically has to prove how smart he is, especially to himself and displays what appears to be an inferiority complex in contrast to his overconfident demeanour. He has made it his one and only goal to degrade others, especially Batman, as being stupider than him with with either arrogant insults designed to lower his victims self-esteem or using the unfounded results from his tests (death traps) as evidence of this. In a moment of complete self-righteousness he claims his tests were for the good of society by weeding out those who are intelligent and those who fail, who are by Nigma's definition "stupid", always die. Nigma's magnificently over-fed ego is never damaged, ignoring that he has been defeated, humiliated and imprisoned multiple times, he constantly believes he will come out on top, never thinking history would repeat itself. He is not above cowardice or dropping his arrogant façade by pathetically pleading.
Appearance:
In Arkham Origins, Enigma had brown hair with glasses. He wore a purple vest with his GCPD tag on his neck, a white shirt and tie, fingerless gloves, and on his left hand he wore two watches on his wrist. He also wore dark green pants with keys on his belt loops, and brown shoes.
9 notes
·
View notes
Text
File: Ben 10
SCP#: AGX
Code Name: Ben Tennyson, Hero of the Omnitrix
Object Class: Keter
Universe of Origin: Υ-17: "Broken Masquerade"
Special Containment Procedures: SCP-AGX-Hero has proven to be quite resilient and much smarter than he mostly acts. The Global Occult Coalition and PENTAGRAM have already tried containing him on multiple events, all of which have failed. Instead, the Foundation is to keep a friendly but distant relationship with SCP-AGX-Hero. Due to his grandfather being a veteran of the Global Occult Coalition he has been trusted by the GOC and the Foundation to keep an eye of SCP-AGX-Hero and to never use SCP-AGX to commit crimes. Mobile Task Force Athena-9 “Justice is Dead” is responsible for taking out SCP-AGX if he ever shows signs of becoming evil.
Description: SCP-AGX is a piece of anomalous technology that resembles a wristwatch; created by an unknown alien, from an unknown species, from an unknown world. All that is known is that SCP-AGX, despite being technological, is symbiotic in nature, being able to attach to anyone who is close to it. Once this happens, they are bonded with SCP-AGX and can utilize its capabilities to its full extent. The current host is Person of Interest: Ben Tennyson who has been labeled as SCP-AGX-Hero.
SCP-AGX-Hero is able to utilize SCP-AGX to select any of several possibly hundreds of DNA samples collected. Once a selection is made SCP-AGX-Hero’s DNA will be rewritten with the DNA sample making them a pure alien from the DNA sample. With this they will have the body, strengths, abilities, and weaknesses of the alien as if they were always that species. List of alien species SCP-AGX can transform into is quite vast as the Foundation has only witnessed a few of the suspected hundreds. Please see Addendum X-78 for details.
SCP-AGX was discovered in 2005 and has since had a minor but noticeable impact on the world, more specifically the United States. A regrettable result was the fact that due to SCP-AGX-Hero having access to multiple alien species, leading to civilians believing that there were multiple heroes and creatures fighting villains and hostile anomalies. This confusion, especially the fact that none of the aliens SCP-AGX-Hero transforms into have been identified by civilians, or the Foundation, has resulted in the public asking all the wrong questions.
However, SCP-AGX-Hero though young, has proven competent enough to defend himself and his family. That and due to his uncle, Person of Interest: Max Tennyson being a veteran of the Global Occult Coalition’s galactic division he has access to several weapons made with captured alien tech. Apparently, they were all given to him as a reward for his many feats and years of service; a decision that has angered many members of Administrative Staff here at the Foundation. In conclusion to make an enemy of SCP-AGX is not in the Foundation’s interest, for now, we will observe and wait for an opportunity to see how SCP-AGX can be properly utilized, if at all.
.
SCP Horror Movie Files Hub
#DZtheNerd#SCP: Horror Movie Files#SCP: HMF#SCP Foundation#SCP Fanfiction#SCP AU#SCP#SCP Fanmade#SCP GoI#SCP Group of Interest#Group of Interest#Groups of Interest#PENTAGRAM#Global Occult Coalition#Ben 10#Action#Adventure#Sci Fi#Sci-Fi#Science Fiction#Cartoon#Classic#Comedy#SCP-AGX#Keter#Υ-17: “Broken Masquerade”#Universe Υ-17: “Broken Masquerade”
4 notes
·
View notes
Text
Snippet of the DJ Five Pebbles AU I've been working on today can be found below.
It was only when Pebbles deemed the messenger sufficiently recovered—or, rather, when it literally started trying to climb the walls in a bid for freedom via stabbing them with its needles—and had just finished helping it leave through his access shaft when he had to admit defeat and reluctantly accept that the idea that had been percolating in the back of his neurons for the past cycle or so: the idea that Seven Red Suns was not only fallible, but had, more than likely, sent him the wrong pearl.
The realization was…disappointing. Beyond the fact that it meant Pebbles’ plans to circumvent the self-destruction taboos needed to be delayed—which was in itself massively disappointing, and even slightly infuriating—the idea of hiding information behind music by way of melody and notation was just such a cool concept. Melody and Harmony could be used to stand in for the polynucleotide chains comprising the deoxyribonucleic acid making up the genome-altering organism. The proper amounts and corresponding placements of adenine, cytosine, and guanine could then be directly notated via placement of notes on a staff, and a different note could be substituted for thymine to account for the fact that musical notes only went up to “G.” Or perhaps thymine could instead be substituted with rests or other symbols, or by the use of accidentals or ornaments. Or it could even be left out entirely, requiring the use of iteration to puzzle out its correct placement much in the way the Triangulators tried to puzzle out the Solution indirectly!
Entire measures and musical phrases could be thrown in that contained no code, only acting as further encryption for the unaware. Repeat signs, a dal segno, or even da capo could be used to save space and denote how specific polynucleotide chains required repetition! Or that the specific segments of the deoxyribonucleic acid needed careful attention because they were more prone to causing the sorts of out of control division and multiplication in cell division that led to rot! There were so many interesting possibilities… and yet Suns had employed none of them.
Because the pearl, with its pretty, golden sheen and coloration, contained no such clever puzzles. It was just as it appeared to be on the surface, and within the audio track: a piece of music.
Though… an admittedly interesting piece of music.
#mostly posting because i am super proud of this part#but also unsure if i will get to complete the story any time soon#so i wanted to go ahead and share it#rain world#dj five pebbles au#fanfiction
6 notes
·
View notes
Note
Okay, so I have to ask what you think of Mayuri's weird computer-organ-construct from the Fade to Black movie. How does it work? Is it one of those surreal movies-only choices, or does it appear in the filler episodes somewhere? I don't think so, but I am not as up on the interior decorating choices of the Twelfth Division as you are.
ippoddity: I think that version of the computer only features in Fade to Black, but I don’t think it’s necessarily a super special movie-only choice. Honestly, Mayuri probably changes up the peripheral hardware for his computer every month. His research is proprietary and he doesn't want anyone else using it or accessing it. If you can’t even figure out how to type anything into the computer, then you can’t steal it! Also, the lab gets blown up multiple times anyway, so nothing sticks around for long. Every time Mayuri upgrades his own hardware and peripherals, the lab gets upgraded too. The 12th computer is a living module whose parts he switches out on the regular. It’s an “organ” on multiple levels. It just so happens that at one point, Mayuri decided to take it extremely literally and it took the form of a musical organ, as well as a computer organ, and a biological organ.
Imagine being some poor lackey in the 12th who is constantly trying to keep up with their ever-changing workstation though.

“You’re telling me I have to learn how to play the piano this month??”
--
whipplefilter: In addition to being an organ^3, I'm sure its construction adheres to some kind of arcane numerological pattern. I'm thinking about the organ at Tsukiji Hongwanji, because Buddhist temples are not typically outfitted with organs:

Regarding the Tsukiji Hongwanji organ: "The pipes on either side form six mountains that represent the six Chinese characters 南・無・阿・弥・陀・仏 (na mu a mi da butsu). There are 48 pipes in the center of each side, and they represent the 48 Vows which is a central sutra of Jodo Shinshu" (matcha-jp).
Which is. SOOOOOO EXTRAAAA! And Mayuri, of course, is also that extra. Therefore, the organ must clearly be an ornate way of inscribing lab secrets somewhere inscrutable yet in plain sight. What is the numerological pattern? I mean, that's between Mayuri and his organ... and probably Nemu. Maybe it's code for "fuck Urahara Kisuke." Maybe it's the Gotei equivalent of the nuclear codes (not for the Kidou Cannon, which is mere child's play).
11 notes
·
View notes
Text
If you ever wonder how I go about patching the timeline, here's a rough idea of how my thought process works in written form:
Based on HW2 trailer, energy well panel can be seen in SL facility elevator so assume SL to be point of introduction for Mimic
SL split in 2 instances in Parlourverse: SL past non-game sets up intro of Afton to assume overarching antagonist role thru Lucian, SL game-ver follows Meera as Eggs Benedict
Cassie mentions dad had wrench, wrench matches panel, panel appears in Ruin and HW2’s SL
Float Cassie Dad from Meera-era SL to pre-employee purge SB, re-visit when HW2 releases
Mimic source?
Mimic AI contains data of all animatronics, mimicked Afton(?), learning by watching or assimilating (Elder Afton Remnant was destroyed by FuriRosa in PizzaSim location, Elizabeth salvaged the larger fragments of Emelia but needs to find data sources to recreate Elder Afton’s memories and consciousness somehow (creates motive to want Mimic developed and learning from Afton data))
when was the most amount of data gathered to feed Mimic for Parlourverse? UCN
UCN arc location: underground SL facility, multiple entry points based on FNAF4/SL map overlay
Meera’s original entry via Rental facility was destroyed, so UCN entry point must be someplace else (pizzeria? No, pizzeria appears to be same as the PizzaSim location, requires Henry intervention) Afton house? (could work, may have been abandoned by this point)
how did Router get in then? Track his movements from Fazbear Frights to SL facility, he escaped dispelling in FNAF4 arc and went looking for Lucian’s last location for revenge (cross-reference original timeline) (Emelia getting out created a tunnel that let Router in)
Elizabeth had all animatronics built from data stored in mainframe, same info was given to games division for HW and SD (she kept going back to the UCN location to salvage what she could of the animatronics, the ones made by Elder Afton would have data about him that she needs)
Mimic AI potentially emerged as a result of fusing all that data into a ‘parent’ node for programming behaviors in the games for the animatronics (mixed into all the parts scanned in were the original Afton made animatronics, allowing Mimic AI to assimilate data about Elder Afton)
servers holding it are locked with energy well panels while Elizabeth attempts to have it trained to focus on mimicking Elder Afton and ‘restore’ him
(where is master file? He escaped the facility during UCN arc with Elizabeth to be installed into Pizzaplex as the governing AI; a copy of him went into the games division server but was consumed by Mimic over time so Mimic now can mimic Lucian Master File (this is important because it’s a flawed mimic as MF removed things from himself that Digi retains))
So where is Mimic AI right now?
A.I. is housed in servers at game studio branch, producing coding for the SD animatronics. The game coding was scrubbed after Alex gained access to the source code and cut the network connection between it and the Mimic so he could quarantine it in-game and destroy the code.
Where is the Mimic animatronic? Trace back events to locate most probable period it could have been constructed and where, then path forward to determine where it ended up.
---------
That's as far as I got as my brain got distracted so now I have to sit and reel it back in and think about the mechanical part of the Mimic.
3 notes
·
View notes
Text
So like, when I was in grade school I read this book. It was about a group of kids in the same classroom. The teacher didn't believe in tests because she preferred to see how the students learn from homework assignments.
One student constantly got an A+ on every assignment. Eventually, 3 other students cornered him and asked how he could pass his assignments like that. He explained that he didn't have time to do the assignments himself, so he built a machine that did it for him. It even wrote the answers in his handwriting. The other students wanted to use this machine too. They also had extracurriculars that took up time, and one of the students was struggling with understanding the materials in general.
He eventually let them use it. He trained the machine to write in their handwriting as well. Over the course of the school year, the students basically used the machine for every assignment. Not even glancing at their textbooks. The teacher noticed something was up and decided to go against her original plan and give them a test. When they did the test, only the first boy passed it, the rest did not. They had relied on the machine so much that they couldn't even recognize lessons from the school day, after all, why would they need to learn in class when the machine would just cover any gaps they missed?
They knew that the teacher was onto them for CHEATING, because that's what they were doing, cheating on their assignments. They got scared of academic failure, being held back a year, getting detention, all that jazz. So, they decide to unplug the machine and never use it again.
Only, the machine learned how to be energy efficient. It wouldn't shut off. The kids then do the only thing they could think of and threw the machine into the Grand Canyon. Of course, they were caught, got into big trouble, had to spend a weekend cleaning parts out of the canyon, had to repeat the year. They set themselves back that far, because they couldn't bother to do the work themselves.
I read this when I was 11? Maybe 12? And when I read this, I thought about what I would have done in this situation. If I had access to a machine that would do my homework for me, would I use it? I realized that I wouldn't. Because if I did, I would have to keep using it forever.
If I missed out on the lesson of, say simple addition and subtraction, then I would be completely lost next year with multiplication and division. Then the next year I wouldn't be able to understand fractions or geometry or balancing chemical equations or ANYTHING later on that needed the basic building blocks of addition and subtraction. I decided it wasn't worth it and would probably be more exhausting trying to keep up the lie of using the machine than it would be to just, do my work in the first place.
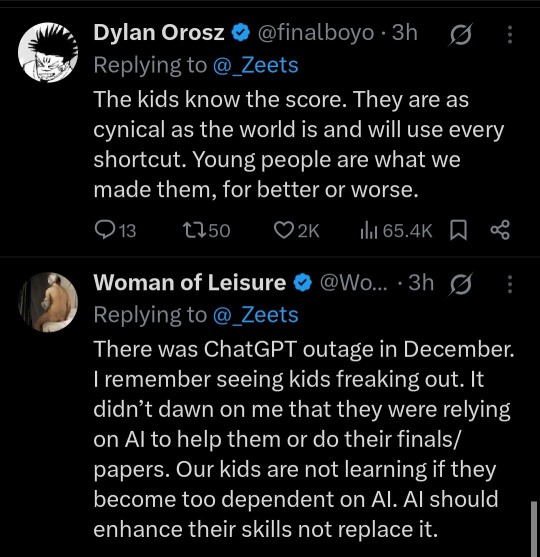
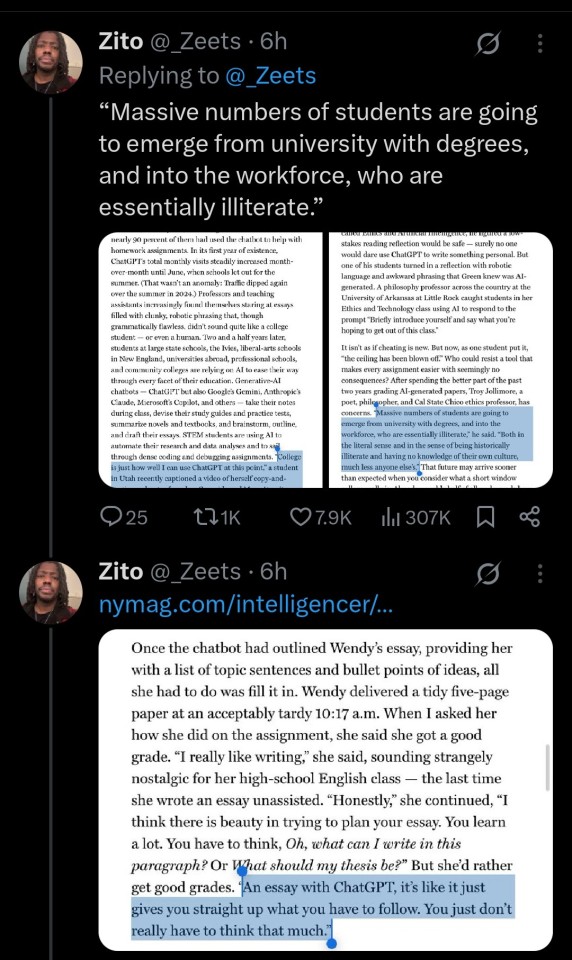
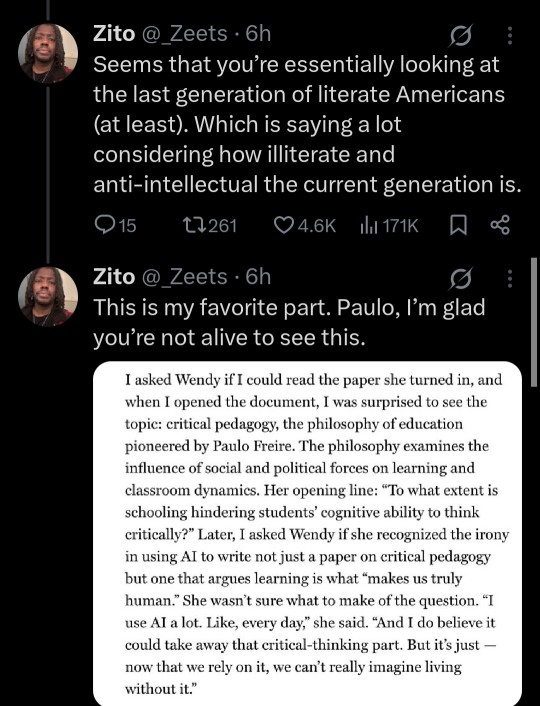
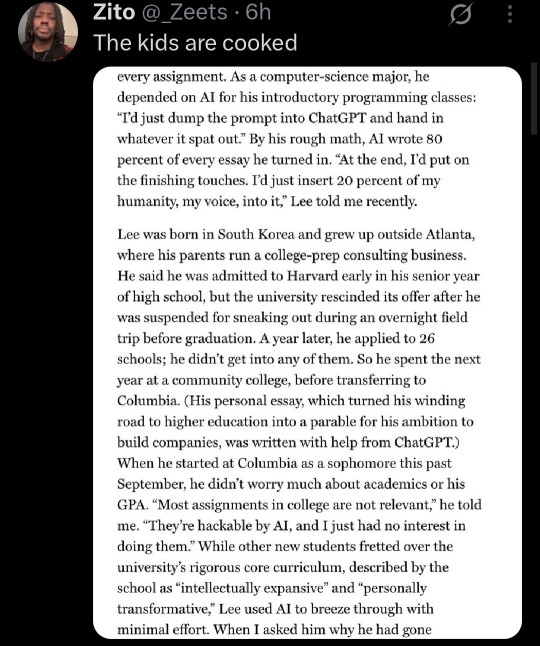
Now, seeing this generative ai wave happening in academic settings, I am incredibly worried about our future professionals. Even if you went and got a master's degree in a specific field of study, if you did it with ai then you have no clue how to do the jobs hiring for that study. Even if you have a coding degree, what are you going to do when you get hired and your boss gives you a piece of code to fix and it all looks basically like hieroglyphics? What happens when you plug that into chatgpt and the "fix" it gives you doesn't work? What happens when you have to ACTUALLY think through the problem and can't actually do the work you got hired for because you have no clue how to do it in the first place?
You fail. You fail at the job. You fail at the thing you are supposed to be an expert in. You got a job you have no qualifications for and now it shows, to you, to your coworkers, to your boss, to everyone. When that happens, you lose your job and everything you have that relies on that job to pay for it.
My point being, you're not escaping the F by using chatgpt, you're simply passing it on to a more important project. Take the F in school and actually learn something instead of pushing it to something more devastating.
#cannot remember the name of that book#i can remember the critical thinking that went into my experience with it though
560 notes
·
View notes
Text
The Complete Toronto Bathroom Renovation Planning Guide
Renovating a bathroom in Toronto can transform your home, boosting both its functionality and value. However, the process involves navigating local regulations, understanding costs, and making informed design choices. This comprehensive guide walks you through every step of planning a bathroom renovation in Toronto, tailored to the city’s unique market, climate, and regulations.
1. Understanding Your Goals and Needs
Before diving into a bathroom renovation, clarify your objectives. Are you aiming to modernize an outdated space, increase accessibility, or add luxury features? Consider the following:
Functionality: Do you need more storage, better lighting, or a layout that accommodates multiple users?
Aesthetics: Are you drawn to minimalist, modern, or traditional designs?
Budget: What’s your financial range, including a buffer for unexpected costs?
Timeline: Do you have a deadline, such as hosting guests or selling your home?
Resale Value: In Toronto’s competitive real estate market, a well-designed bathroom can increase your home’s appeal. Features like double vanities or walk-in showers are popular among buyers.
Tip: Create a mood board with inspiration from platforms like Pinterest or Houzz to define your style. For Toronto homeowners, consider designs that balance timeless appeal with modern functionality to suit the city’s diverse tastes.
2. Setting a Realistic Budget
Bathroom renovation costs in Toronto vary widely based on size, materials, and labor. As of 2025, expect to spend:
Basic Renovation: $10,000–$20,000 for cosmetic updates (new fixtures, paint, basic tiling).
Mid-Range Renovation: $20,000–$40,000 for new vanities, flooring, and partial plumbing or electrical work.
Luxury Renovation: $40,000–$80,000+ for high-end materials, custom cabinetry, and features like heated floors or smart showers.
Key Cost Factors
Labor: Toronto’s skilled labor market is expensive, with contractors charging $50–$100/hour.
Materials: High-quality tiles, fixtures, and vanities drive up costs. For example, porcelain tiles cost $5–$20/sq.ft., while natural stone can exceed $50/sq.ft.
Permits: Structural changes or plumbing/electrical work may require permits, costing $500–$2,000.
Unexpected Issues: Older Toronto homes (pre-1980s) may have outdated plumbing or asbestos, adding $1,000–$5,000+ to address.
Tip: Get quotes from at least three Toronto-based contractors. Factor in a 10–20% contingency fund for surprises, especially in older homes in areas like Cabbagetown or The Annex.
3. Navigating Toronto’s Building Regulations
Toronto has strict building codes and permit requirements, especially for bathrooms due to plumbing, electrical, and ventilation standards. Key considerations include:
Permits: Required for structural changes, relocating plumbing/electrical systems, or adding windows. Contact the Toronto Building Division or visit toronto.ca/building for details.
Plumbing: Must comply with the Ontario Building Code, including proper drainage and venting. For example, toilets require a 3-inch drain line.
Ventilation: Bathrooms must have a window or an exhaust fan vented to the exterior to prevent mold, a concern in Toronto’s humid summers.
Electrical: GFCI outlets are mandatory near water sources. Hire a licensed electrician to meet Electrical Safety Authority (ESA) standards.
Tip: Check if your home is in a heritage district (e.g., Rosedale or Forest Hill), as additional approvals may be needed for exterior changes like new windows.
4. Choosing a Design and Layout
Toronto’s diverse housing stock—from compact condos to spacious Victorian homes—impacts bathroom design. Consider these layout tips:
Small Bathrooms (Condos, Townhouses): Opt for space-saving features like wall-mounted vanities, corner sinks, or sliding glass shower doors. A 5’x8’ bathroom is common in Toronto condos.
Large Bathrooms (Detached Homes): Incorporate luxury elements like freestanding tubs, double vanities, or walk-in showers with bench seating.
Accessibility: With Toronto’s aging population, features like grab bars, curbless showers, and non-slip flooring are increasingly popular.
Popular Design Trends in Toronto (2025)
Neutral Tones: Whites, grays, and beiges dominate for a clean, timeless look.
Bold Accents: Matte black fixtures or patterned tiles add personality.
Eco-Friendly Features: Low-flow toilets and LED lighting align with Toronto’s sustainability goals.
Smart Technology: Smart mirrors, heated floors, and touchless faucets are gaining traction in luxury renovations.
Tip: Visit local showrooms like Taps Bath Centre or Ginger’s in Toronto to explore fixtures and materials in person.
5. Selecting Materials and Fixtures
Choosing durable, high-quality materials is crucial for Toronto’s climate, where humidity and temperature fluctuations can affect longevity.
Flooring: Porcelain or ceramic tiles are ideal for durability and water resistance. Heated floors are popular for Toronto’s cold winters, costing $10–$20/sq.ft. to install.
Walls: Subway tiles ($5–$15/sq.ft.) or large-format tiles ($10–$30/sq.ft.) are trendy and easy to clean.
Vanities: Custom or semi-custom vanities from local suppliers like Cutler Kitchen & Bath offer durability and style.
Fixtures: Brands like Moen, Kohler, or Delta are reliable choices. Consider water-efficient models to comply with Toronto’s water conservation bylaws.
Tip: Source materials from local suppliers like Stonehooker or Ciot to support Toronto businesses and reduce shipping delays.
6. Hiring a Contractor
Finding a reliable contractor in Toronto is critical. Look for:
Licensing and Insurance: Ensure they’re licensed with the City of Toronto and carry liability insurance.
Experience: Choose contractors familiar with Toronto’s building codes and older homes.
References: Check reviews on platforms like HomeStars or ask for past project photos.
Contracts: Get a detailed contract outlining scope, timeline, and payment schedule.
Recommended Toronto Contractors (based on reputation, not endorsement):
Avenue Road Construction: Known for high-end renovations.
Build Toronto: Specializes in condo and residential projects.
Maple Reno: Offers budget-friendly options with good reviews.
Tip: Verify contractor credentials through the Better Business Bureau or the City of Toronto’s contractor licensing database.
7. Planning the Timeline
A typical Toronto bathroom renovation takes 2–8 weeks, depending on scope:
Planning and Permits: 1–3 weeks.
Demolition: 1–3 days.
Plumbing/Electrical Rough-Ins: 3–7 days.
Installation (Tiling, Fixtures, etc.): 1–3 weeks.
Finishing Touches: 3–5 days.
Delays can occur due to permit approvals, material shortages, or unexpected issues like mold or outdated wiring, common in Toronto’s older homes.
Tip: Schedule renovations during spring or fall to avoid peak contractor demand in summer and material delays in winter.
8. Sustainability and Energy Efficiency
Toronto’s Green Standard encourages eco-friendly renovations. Consider:
Water-Saving Fixtures: Low-flow toilets (1.28 GPF) and showerheads (1.5–2 GPM) reduce water bills.
LED Lighting: Energy-efficient and long-lasting, ideal for Toronto’s high electricity costs.
Insulation: Proper insulation around pipes prevents heat loss, crucial for winter.
Tip: Check for rebates through Toronto Hydro or the Home Energy Loan Program (HELP) for energy-efficient upgrades.
9. Adding Value to Your Toronto Home
A well-executed bathroom renovation can yield a 50–70% return on investment in Toronto’s hot real estate market. Focus on universal appeal:
Neutral Designs: Avoid overly trendy finishes that may not suit all buyers.
Storage: Built-in niches or vanities with ample storage are a big draw.
Quality: Invest in durable materials to avoid repairs that could deter buyers.
Tip: Consult a local realtor to understand what features are most desirable in your neighborhood, such as Leaside or Leslieville.
10. Final Checklist Before Starting
[ ] Finalize budget and secure financing.
[ ] Obtain necessary permits from the City of Toronto.
[ ] Hire a licensed contractor with a clear contract.
[ ] Order materials early to avoid delays.
[ ] Plan temporary bathroom access (e.g., use a secondary bathroom or neighbor’s facilities).
[ ] Communicate with neighbors about noise or disruptions, especially in condos.
Conclusion
A bathroom renovation in Toronto is a significant investment that requires careful planning to balance aesthetics, functionality, and compliance with local regulations. By setting clear goals, budgeting wisely, and hiring reputable professionals, you can create a space that enhances your home’s comfort and value. Whether you’re in a downtown condo or a North York bungalow, this guide equips you with the knowledge to navigate the process confidently.
1 note
·
View note
Text
Finding the Best Roofing Contractor in New Jersey.

New Jersey’s harsh winters, humid summers, and occasional storms put roofs to the test, making it essential to hire a reliable roofing contractor for repairs, replacements, or installations. Choosing the right professional ensures quality work, durability, and peace of mind. Here’s a step-by-step guide to finding the best roofing contractor in New Jersey, with a spotlight on Better Path Construction, a potential option for your roofing needs.
1. Verify Licensing and Insurance
A reputable roofing contractor must be licensed by the New Jersey Division of Consumer Affairs and carry both liability insurance and workers’ compensation coverage. This protects you from financial liability in case of accidents or damage during the project. Before hiring, request proof of these credentials to ensure compliance with state regulations.
2. Check Local Experience and Reputation
Contractors familiar with New Jersey’s climate and building codes are better equipped to recommend durable materials and techniques. Look for companies with a strong local presence and positive customer feedback. Platforms like Yelp, Angie’s List, or the Better Business Bureau (BBB) offer insights into a contractor’s reliability. Ask for references from past clients to confirm their track record.
3. Explore Better Path Construction
For homeowners considering local options, Better Path Construction stands out as a potential choice. While specific details about their roofing services are not fully outlined in available data, their website suggests a focus on construction services, which may include roofing. To confirm their expertise, contact them directly to inquire about their experience with New Jersey roofing projects, certifications, and customer reviews. Always verify their licensing and insurance before proceeding.
4. Compare Multiple Estimates
Obtain at least three detailed quotes from different contractors to compare pricing, materials, and scope of work. A transparent estimate reflects professionalism and helps avoid unexpected costs. Be cautious of unusually low bids, as they may indicate subpar materials or shortcuts. Ensure the contractor explains the proposed materials and their suitability for New Jersey’s weather.
5. Confirm Certifications and Warranties
Top contractors often hold certifications from leading manufacturers like GAF, Owens Corning, or CertainTeed, which can unlock extended warranties (e.g., 25-year or lifetime). These certifications signal expertise and access to high-quality materials. Ask about both manufacturer and workmanship warranties, and ensure they are provided in writing. When evaluating Better Path Construction, inquire if they offer such certifications to guarantee long-term value.
6. Ask the Right Questions
Engage contractors with specific questions to gauge their professionalism:
How many years have you served New Jersey homeowners?
What roofing materials do you recommend for my home?
Can you provide a timeline and cleanup plan?
Do you have experience with my preferred roofing type (e.g., asphalt shingles, metal, slate)?
These questions help assess their expertise and commitment to customer satisfaction.
Why Choose the Best?
Hiring the best roofing contractor, like potentially Better Path Construction, ensures your roof withstands New Jersey’s challenging climate while enhancing your home’s value and safety. A reliable contractor delivers quality craftsmanship, uses durable materials, and provides clear communication throughout the project.
Final Tips
Research Thoroughly: Use online resources, word-of-mouth recommendations, and professional networks (e.g., local realtors) to identify trusted contractors.
Avoid Scams: Be wary of contractors who demand large upfront payments or lack a physical address. Verify Better Path Construction’s legitimacy by checking their business details and reviews.
Get Everything in Writing: A detailed contract outlining costs, materials, timeline, and warranties is non-negotiable.
For a potential roofing partner, visit Better Path Construction to explore their services. Contact them to confirm their roofing expertise, request a free estimate, and ensure they meet New Jersey’s licensing and insurance standards. By following these steps, you’ll find the best roofing contractor to protect your home for years to come.
0 notes
Text

🛰️ Entry 003 – The Crash Reveals
Filed: 06 October 2022 Archive Code: CR-IN-2202-I Author: Kalameet Lund, Science Officer Clearance: Internal Eyes Only Location: Near Samarkand Heights, Uzbekistan
“The skies did not break open. They whispered.”
The anomaly zone was located in the highland glade east of Samarkand—accessible, unguarded, and marked only by signs nature could not have made. Vegetation was flattened in an outward spiral. Soil samples returned readings consistent with atmospheric breach-level irradiation, and molecules in the surrounding terrain exhibited directional lattice disruption—suggesting a controlled descent, not a high-velocity impact.
There was no crater. No debris field. Only a long trench of upturned earth, and at its center, a structure unlike any constructed by human hands.
Our recovery team moved under blackout protocols. Lead-lined suits. Noise-dampened transport. No digital signatures. I oversaw the initial contact.
What we found was a half-submerged form—collapsed inward, as though its internal geometry had failed under conditions we cannot replicate. It folded, but not randomly. Its collapse pattern followed a symmetry our engineers have since called “incompatible with material fatigue.”
Its surface was comprised of unknown alloys, warm to the touch despite ambient temperature, and laced with electromagnetic echoes that have since interfered with multiple Initiative lab systems. We do not yet know whether the structure was a vehicle, a probe, or something else entirely. We only know this: it was not made by us.
Containment and Cover Measures
Local Uzbek authorities were redirected with fabricated geological reports of a subsurface gas explosion. Satellite reconnaissance was intercepted and reflagged as part of a “joint research mineral survey.” Civilian witnesses were minimal and are being monitored.
Leak probability remains low. Internal security protocols remain active.
International Response
Simultaneous to the recovery operation, the UN Security Council convened in emergency session. What could have become a moment of global solidarity fractured instantly. Accusations were exchanged. The United States, China, and Russia each accused the others of concealment, sabotage, and illegal militarization of space.
There was no consensus. No resolution. No joint statement.
What we witnessed was not cooperation, but a rehearsal of division.
Strategic Summary
Confirmation of an extraterrestrial-origin structure
Partial recovery of advanced materials
No biological or hostile activity detected, but EM signatures are strong and sustained
Global diplomatic posture degrading rapidly
Initiative will not claim the site. Strategic silence remains policy.
We will continue to observe. We will continue to gather.
We will speak only when the world is ready to listen.
Next Directive
Secure transfer of recovered material to Initiative deep lab facility Theta-6
Begin advanced spectrographic and structural sequencing
Prepare escalation protocols for emergent biological vectors, should any arise
#TerraInvicta#InitiativeChronicle#UNSecurityCouncil#AlienArrival#GeoPolitics#SciFiNarrative#SilentManeuvers#CrisisResponse#DiplomaticChaos#FactionPolitics#NarrativeGaming#PhillipMinton#StrategyRPG#TacticalEspionage
0 notes
Text
Manus AI agent: breakthrough in China's agentic AI
New Post has been published on https://thedigitalinsider.com/manus-ai-agent-breakthrough-in-chinas-agentic-ai/
Manus AI agent: breakthrough in China's agentic AI


Manus AI agent is China’s latest artificial intelligence breakthrough that’s turning heads in Silicon Valley and beyond. Manus was launched last week via an invitation-only preview, and represents China’s most ambitious entry into the emerging AI agent market.
Unlike anything seen to date, the Manus AI agent doesn’t just chat with users – it is allegedly capable of independently tackling complex multi-step tasks with minimal human guidance.
Developed by Chinese startup Butterfly Effect with financial backing from tech giant Tencent Holdings, Manus AI agent has captured global attention for its ability to bridge the gap between theoretical AI capabilities and practical, real-world applications. It uses an innovative multi-model architecture that combines the strengths of multiple leading language models.
Breakthrough autonomous task execution
In a post on X, Peak Ji Yichao, co-founder and chief scientist at Butterfly Effect, said that the agentic AI was built using existing large language models, including Anthropic’s Claude and fine-tuned versions of Alibaba’s open-source Qwen.
Its multi-model nature allows Manus to use different AI strengths according to what’s demanded of it, resulting in more sophisticated reasoning and execution capabilities.
“The Manus AI agent represents a fundamentally different approach to artificial intelligence,” CNN Business stated. According to coverage, Manus “can carry out complex, multi-step tasks like screening resumés and creating a website,” and “doesn’t only generate ideas but delivers tangible results, like producing a report recommending properties to buy based on specific criteria.”
Real-world performance assessment
In an extensive hands-on evaluation, MIT Technology Review tested the Manus AI agent in three distinct task categories: compiling comprehensive journalist lists, conducting real estate searches with complex parameters, and identifying candidates for its prestigious Innovators Under 35 program.
“Using Manus feels like collaborating with a highly intelligent and efficient intern,” wrote Caiwei Chen in the assessment. “While it occasionally lacks understanding of what it’s being asked to do, makes incorrect assumptions, or cuts corners to expedite tasks, it explains its reasoning clearly, is remarkably adaptable, and can improve substantially when provided with detailed instructions or feedback.”
The evaluation revealed one of the Manus AI agent’s most distinctive features – its “Manus’s Computer” interface, which provides unprecedented transparency into the AI’s decision-making process.
The application window lets users observe the agent’s actions in real time and intervene when necessary, creating a collaborative human-AI workflow that maintains user control while automating complex processes.
Technical implementation challenges
Despite impressive capabilities, the Manus AI agent faces significant technical hurdles in its current implementation.MIT Technology Reviewdocumented frequent system crashes and timeout errors during extended use.
The platform displayed error messages, citing “high service load,” suggesting that computational infrastructure remains a limitation.
The technical constraints have contributed to highly restricted access, with less than 1% of wait-listed users receiving invite codes – the official Manus Discord channel has already accumulated over 186,000 members.
According to reporting from Chinese technology publication36Kr, the Manus AI agent’s operational costs remain relatively competitive at approximately $2 per task.
Strategic partnership with Alibaba Cloud
The creators of the Manus AI agent have announced a partnership with Alibaba’s cloud computing division. According to a South China Morning Post report dated March 11, “Manus will engage in strategic cooperation with Alibaba’s Qwen team to meet the needs of Chinese users.”
The partnership aims to make Manus available on “domestic models and computing platforms,” although implementation timelines remain unspecified.
Parallel advancements in foundation models
The Manus-Alibaba partnership coincides with Alibaba’s advances in AI foundation model technology. On March 6, the company published its QwQ-32B reasoning model, claiming performance characteristics that surpass OpenAI’s o1-mini and rivalling DeepSeek’s R1 model, despite a lower parameter count.
CNN Businessreported, “Alibaba touted its new model, QwQ-32B, in an online statement as delivering exceptional performance, almost entirely surpassing OpenAI-o1-mini and rivalling the strongest open-source reasoning model, DeepSeek-R1.”
The claimed efficiency gains are particularly noteworthy – Alibaba says QwQ-32B achieves competitive performance with just 32 billion parameters, compared to the 671 billion parameters in DeepSeek’s R1 model. The reduced model size suggests substantially lower computational requirements for training and inference with advanced reasoning capabilities.
China’s strategic AI investments
The Manus AI agent and Alibaba’s model advancements reflect China’s broader strategic emphasis on artificial intelligence development. The Chinese government has pledged explicit support for “emerging industries and industries of the future,” with artificial intelligence receiving particular focus alongside quantum computing and robotics.
Alibaba will invest 380 billion yuan (approximately $52.4 billion) in AI and cloud computing infrastructure in the next three years, a figure the company notes exceeds its total investments in these sectors during the previous decade.
As MIT Technology Review’s Caiwei Chen said, “Chinese AI companies are not just following in the footsteps of their Western counterparts. Rather than just innovating on base models, they are actively shaping the adoption of autonomous AI agents in their way.”
The Manus AI agent also exemplifies how China’s artificial intelligence ecosystem has evolved beyond merely replicating Western advances. Government policies promoting technological self-reliance, substantial funding initiatives, and a growing pipeline of specialised AI talent from Chinese universities have created conditions for original innovation.
Rather than a single approach to artificial intelligence, we are witnessing diverse implementation philosophies likely resulting in complementary systems optimised for different uses and cultural contexts.
#000#adoption#agent#Agentic AI#agents#AGI#ai#ai agent#AI AGENTS#AI and cloud#AI and cloud computing#ai talent#Alibaba#alibaba cloud#anthropic#applications#approach#architecture#artificial#Artificial Intelligence#assessment#attention#autonomous#autonomous ai#billion#bridge#Business#butterfly#channel#China
1 note
·
View note
Text
Basics of R programming
Understanding the basics of R programming is crucial for anyone looking to leverage its capabilities for data analysis and statistical computing. In this chapter, we'll explore the fundamental elements of R, including its syntax, variables, data types, and operators. These are the building blocks of any R program and are essential for developing more complex scripts and functions.
R Syntax
R's syntax is designed to be straightforward and user-friendly, especially for those new to programming. It emphasizes readability and ease of use, which is why it's popular among statisticians and data scientists.
Comments: Comments are used to annotate code, making it easier to understand. In R, comments begin with a # symbol:# This is a comment in R
Statements and Expressions: R executes statements and expressions sequentially. Statements are typically written on separate lines, but multiple statements can be written on a single line using a semicolon (;):x <- 10 # Assigning a value to variable x y <- 5; z <- 15 # Multiple statements in one line
Printing Output: The print() function is commonly used to display the output of expressions or variables. Simply typing the variable name in the console will also display its value:print(x) # Displays the value of x x # Another way to display x
Variables in R
Variables are used to store data values in R. They are essential for performing operations, data manipulation, and storing results.
Creating Variables: Variables are created using the assignment operator <- or =. Variable names can contain letters, numbers, and underscores, but they must not start with a number:num <- 100 # Assigns the value 100 to the variable num message <- "Hello, R!" # Assigns a string to the variable message
Variable Naming Conventions: It’s good practice to use descriptive names for variables to make the code more readable:total_sales <- 500 customer_name <- "John Doe"
Accessing Variables: Once a variable is created, it can be used in expressions or printed to view its value:total_sales <- 1000 print(total_sales) # Outputs 1000
Data Types in R
R supports a variety of data types that are crucial for handling different kinds of data. The main data types in R include:
Numeric: Used for real numbers (e.g., 42, 3.14):num_value <- 42.5
Integer: Used for whole numbers. Integer values are explicitly declared with an L suffix:int_value <- 42L
Character: Used for text strings (e.g., "Hello, World!"):text_value <- "R programming"
Logical: Used for Boolean values (TRUE or FALSE):
is_active <- TRUE
Factors: Factors are used for categorical data and store both the values and their corresponding levels:status <- factor(c("Single", "Married", "Single"))
Vectors: Vectors are the most basic data structure in R, and they can hold elements of the same type:num_vector <- c(10, 20, 30, 40, 50)
Lists: Lists can contain elements of different types, including vectors, matrices, and even other lists:mixed_list <- list(num_value = 42, text_value = "R", is_active = TRUE)
Operators in R
Operators in R are used to perform operations on variables and data. They include arithmetic operators, relational operators, and logical operators.
Arithmetic Operators: These operators perform basic mathematical operations:
Addition: +
Subtraction: -
Multiplication: *
Division: /
Exponentiation: ^
Modulus: %% (remainder of division)
Example:a <- 10 b <- 3 sum <- a + b # 13 difference <- a - b # 7 product <- a * b # 30 quotient <- a / b # 3.3333 power <- a^b # 1000 remainder <- a %% b # 1
Relational Operators: These operators compare two values and return a logical value (TRUE or FALSE):
Equal to: ==
Not equal to: !=
Greater than: >
Less than: <
Greater than or equal to: >=
Less than or equal to: <=
Example:x <- 10 y <- 5 is_greater <- x > y # TRUE is_equal <- x == y # FALSE
Logical Operators: Logical operators are used to combine multiple conditions:
AND: &
OR: |
NOT: !
Example:a <- TRUE b <- FALSE both_true <- a & b # FALSE either_true <- a | b # TRUE not_a <- !a # FALSE
Working with Data Structures
Understanding R’s data structures is essential for manipulating and analyzing data effectively.
Vectors: As mentioned earlier, vectors are a fundamental data structure in R, and they are used to store sequences of data elements of the same type:numbers <- c(1, 2, 3, 4, 5)
Matrices: Matrices are two-dimensional arrays that store elements of the same type. You can create a matrix using the matrix() function:matrix_data <- matrix(1:9, nrow = 3, ncol = 3)
Data Frames: Data frames are used for storing tabular data, where each column can contain a different type of data. They are akin to tables in a database:df <- data.frame(Name = c("John", "Jane", "Doe"), Age = c(25, 30, 35))
Lists: Lists are versatile structures that can store different types of elements, including other lists:my_list <- list(name = "John", age = 30, scores = c(90, 85, 88))
Uncover more details at Strategic Leap
0 notes
Text
Since the outbreak of COVID-19, remote working has gained ground. It has become the new normal in the society as employees are having to work from their houses, and deliver tasks as efficiently as before. Big companies like Facebook adapted to this style of work when they saw its impact on employees. Companies also benefited from this new style of work as there was no need for office spaces, paying rent annually, or paying for building maintenance, etc. As remote working has stretched on, the hiring process has also changed. After all, companies still need to get the best staff, but how do you hire someone you haven’t physically met? This has made HR tasks also a lot more difficult to accomplish. In this new normal, it is a good idea to turn to tools that can aid in this process of hiring and onboarding. The ideal tool needs to be secure, i.e. so that no data is exposed or leaked online especially confidential information, and it needs to make the process streamlined, simple, and accessible. A good example of these tools is knowledge management tools as they facilitate onboarding processes. Swimm Swimm is a tool that helps engineers (most especially) ramp up to new codebases easily, therefore, leading to optimal productivity for teams, independent work, etc. It enables a smooth development process as it keeps your documents in sync. Features A Snippet Studio This studio helps to easily create walkthroughs, tutorials, etc from your codebase. It brings the spotlight to specific areas in your code and also adds comments to explain the flow of your code and logic. Code Documentation coverage with the Swimm Tree view This feature allows you to rapidly search which file or directory has swimm tutorial and also highlight those areas that lack documentation. Auto Sync Obviously, your code does not remain the same else there is no evolution, hence there is no growth or improvement If the latter is not the case your code evolves. So should your documentation too. With the Auto Sync feature, it suggests automatically the changes to your documentation in line with the evolution of your code and also verifying tutorials to ensure it’s being current or up to date. Bit.ai Bit.ai is a platform built for groups and people to “create, collaborate, and organize” all of their know-how in a single place. With this tool, you can create rapid dynamic notes, documents, wikis, know-how bases, projects, consumer deliverables, technical docs, education publications and consumer portals, even integrating throughout the apps you work with. Features Workflow Solutions They have customizable workflow solutions that allow for varying degrees of user management and multiple workspaces. For an onboarding team, this can be very valuable as it allows varying degrees of access and specific onboarding workspaces with segregated documentation to bring everyone up to speed. Advanced Sharing Their document sharing facilities begin from live document sharing and extend to link tracking and real-time alerts. All documentation shared with onboarding teams is always up-to-date and will alert everyone when something is updated or added. Content Management With tools like smart search and workspace division, Bit can help keep all your content isolated and organized. For dev teams, this can be beneficial while creating and maintaining onboarding documentation, as the various management tools can keep things streamlined and efficient. Tettra Tettra is an internal knowledge base that can assist in organizing knowledge to answer questions and onboard new members through Slack or Microsoft Teams. It is automated as well, so people who ask questions can receive answers instantaneously without having to wait for someone to type everything out. Features Integrations Developers love integrations. Tettra offers integrations for GSuite, Zapier, Google Groups, and many more, making it very compatible with all the different workspaces different dev teams use.
These integrations also make it easier for the tool to run without constant interference or mistakes. Knowledge Management An interesting feature offered by Tettra is that it displays when a piece of information was last verified by someone on the team to be true. This is great for onboarding purposes, as it makes sure that every document is up-to-date and reflective of the current state of the dev team’s progress. API They also offer an API that you can use for personalized further integration to build your own knowledge workflows with the tool. Confluence Confluence is a team workspace that allows teams to create, capture, and collaborate. In a world of remote work and online onboarding, this tool fits right in. It can assist your team structure, organizing, and sharing work, so each crew member has visibility into institutional information and gets the right of entry to the records they want to do their exceptional work. Features Collaboration Confluence is a powerful collaborative editor as it gives you the power to create meeting notes, project plans, product requirements, at the same time as other users are editing and see all the changes at once. Jira Integration Confluence offers integration with Jira for development work and features like issue-tracking and dynamically updating roadmaps. Permissions For onboarding, it’s important to make sure new team members have access to exactly what they need but not more. With Confluence’s permissions features, you can share and protect sensitive content with permission settings. Conclusion As remote work gets more and more popular, a smooth onboarding process with all knowledge being easily accessible makes it better as this helps engineers especially keep up with your company easily and faster, increasing your productivity level in the company. I urge you to start using a tool to aid your onboarding process as this could be a huge boost in your team’s productivity level. Happy Hiring!
0 notes
Text
**Report on Connections Between White Supremacist Groups and Military/Police Forces**
**Introduction**
White supremacist groups, which advocate for racial hierarchy and often engage in violence, have historically sought to infiltrate or recruit members from military and law enforcement institutions. This report examines documented connections, motivations, and responses to this issue, drawing on government reports, academic studies, and watchdog organizations.
---
### **Connections to the Military**
1. **Recruitment and Training**:
White supremacists target the military to gain combat skills. A 2008 FBI report warned that extremists view military service as "a means to acquire training for future conflicts" (FBI, 2008). The 2020 U.S. Senate Armed Services Committee report confirmed that active-duty personnel had ties to extremist groups like the Oath Keepers and Atomwaffen Division (U.S. Senate, 2020).
2. **Notable Cases**:
- In 2020, 12% of individuals charged in domestic terrorism cases had military backgrounds (CSIS, 2020).
- The Michigan governor kidnapping plot (2020) involved multiple veterans linked to the Three Percenters militia (DOJ, 2020).
- A 2021 Pentagon review identified 100+ cases of extremism among service members over a decade (GAO, 2017).
---
### **Connections to Law Enforcement**
1. **Infiltration Risks**:
A 2006 FBI intelligence bulletin warned of white supremacists "deliberately joining law enforcement to disrupt investigations" (FBI, 2006). The Brennan Center (2020) highlighted inadequate screening processes in police departments, enabling extremists to avoid detection.
2. **Documented Incidents**:
- In 2017, off-duty police officers were identified at the Unite the Right rally in Charlottesville (SPLC, 2017).
- The Oath Keepers, implicated in the January 6 Capitol attack, include active/retired law enforcement members (ADL, 2021).
- A 2015 Minneapolis shooting by a KKK-affiliated corrections officer underscored institutional vulnerabilities (NYT, 2015).
---
### **Motivations for Targeting Military/Police**
- **Access to Resources**: Training, weapons, and intelligence enhance operational capabilities.
- **Legitimacy**: Affiliation with respected institutions bolsters recruitment and public perception.
- **Undermining Trust**: Infiltration erodes community confidence in law enforcement (Brennan Center, 2020).
---
### **Efforts to Address Extremism**
1. **Military Reforms**:
- The 2021 Pentagon stand-downs mandated extremism training and established a Counter Extremism Working Group (DOD, 2021).
- Updated Uniform Code of Military Justice policies prohibit extremist activities (DOD Directive 1325.06, 2021).
2. **Law Enforcement Measures**:
- Some departments now use social media audits and background checks (Brennan Center, 2020).
- Challenges persist due to First Amendment protections and union resistance to disciplinary actions (Harvard Law Review, 2020).
---
### **Conclusion**
While most military and law enforcement personnel uphold their duties honorably, even isolated ties to white supremacist groups pose significant risks. Strengthening vetting processes, enhancing transparency, and fostering accountability are critical to mitigating threats. Continued research and interagency collaboration remain essential to address this evolving challenge.
---
**Citations**
- FBI. (2006). *White Supremacist Infiltration of Law Enforcement*.
- FBI. (2008). *Domestic Terrorism: White Supremacist Recruitment of Military Personnel*.
- U.S. Senate Armed Services Committee. (2020). *Extremism in the Military*.
- Brennan Center for Justice. (2020). *Countering Domestic Terrorism*.
- Southern Poverty Law Center (SPLC). (2017). *The Alt-Right in Charlottesville*.
- Anti-Defamation League (ADL). (2021). *Oath Keepers Profile*.
- Department of Defense (DOD). (2021). *Report on Countering Extremism*.
- Government Accountability Office (GAO). (2017). *Extremism in the Military: Prevalence and Responses*.
---
This report synthesizes verified cases and institutional responses, emphasizing the need for proactive measures to safeguard national security and public trust.
0 notes
Text
Understanding Python’s Error Handling and Debugging Techniques
Error handling and debugging are essential skills for writing robust Python code. Python provides various techniques to manage and identify errors that may arise during program execution.
1. Error Types in Python:
Python categorizes errors into two main types:
Syntax Errors: These occur when there is a mistake in the structure of the code. Python’s interpreter catches them before the program runs.
python
print("Hello world" # SyntaxError: unexpected EOF while parsing
Exceptions: These occur during execution when the program encounters a runtime issue. Common exceptions include:
ValueError: Raised when an operation or function receives an argument of the correct type but an inappropriate value.
TypeError: Raised when an operation is performed on an object of inappropriate type.
IndexError: Raised when trying to access an element in a list using an invalid index.
FileNotFoundError: Raised when trying to open a file that doesn’t exist.
Example of a runtime exception:
python
x = 10 y = 0 print(x / y) # ZeroDivisionError: division by zero
2. Using try, except, else, and finally:
Python uses these blocks to handle exceptions:
try block: The code that might raise an exception goes here.
except block: Handles the exception if one occurs.
else block: Executes code if no exception was raised.
finally block: Executes code that should run no matter what (whether an exception was raised or not).
Example:pythonCopyEdittry: number = int(input("Enter a number: ")) result = 10 / number except ZeroDivisionError: print("Cannot divide by zero.") except ValueError: print("Invalid input! Please enter a number.") else: print(f"Result: {result}") finally: print("Execution complete.")
3. Raising Exceptions:
You can raise exceptions explicitly using the raise statement. This is useful for custom error handling or for testing purposes.
Example:pythonCopyEdidef check_age(age): if age < 18: raise ValueError("Age must be 18 or older.") return "Access granted."try: print(check_age(16)) except ValueError as e: print(f"Error: {e}")
4. Custom Exceptions:
You can define your own exception classes by sub classing the built-in Exception class.
Example:pythonclass InvalidAgeError(Exception): passdef check_age(age): if age < 18: raise InvalidAgeError("Age must be 18 or older.") return "Access granted."try: print(check_age(16)) except InvalidAgeError as e: print(f"Error: {e}")
5. Debugging Techniques:
Using pdb (Python Debugger): The Python standard library includes the pdb module, which allows you to set breakpoints and step through code interactively.
Example:
python
import pdb x = 10 y = 0 pdb.set_trace() # Sets a breakpoint print(x / y)
Once the program reaches pdb.set_trace(), the debugger will start, and you can enter commands like n (next), s (step into), c (continue), etc.
Using print Statements: For simple debugging, you can insert print() statements to check the flow of execution and values of variables.
Example:
python
def calculate(a, b): print(f"a: {a}, b: {b}") # Debugging output return a + b
Logging: Instead of using print(), Python’s logging module provides more flexible ways to log messages, including different severity levels (e.g., debug, info, warning, error, critical).
Example:
python
import logging logging.basicConfig(level=logging.DEBUG) logging.debug("This is a debug message") logging.info("This is an info message") logging.error("This is an error message")
6. Handling Multiple Exceptions:
You can handle multiple exceptions in one block or use multiple except clauses.
Example:pythontry: value = int(input("Enter a number: ")) result = 10 / value except (ValueError, ZeroDivisionError) as e: print(f"Error occurred: {e}")
Conclusion:
Understanding Python’s error handling mechanisms and debugging techniques is crucial for writing resilient programs. Using try, except, and other error-handling structures allows you to gracefully manage exceptions, while debugging tools like pdb help identify and resolve issues more efficiently.
WEBSITE: https://www.ficusoft.in/python-training-in-chennai/
0 notes